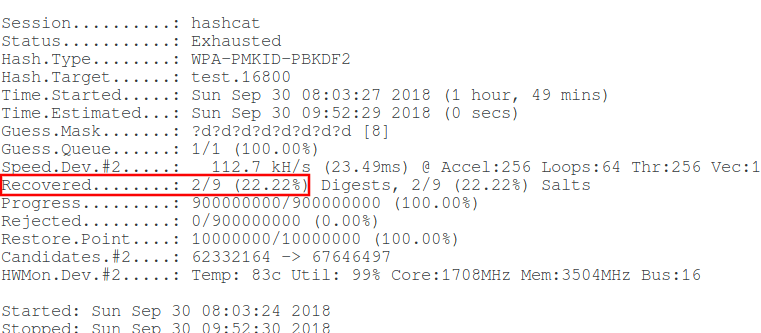
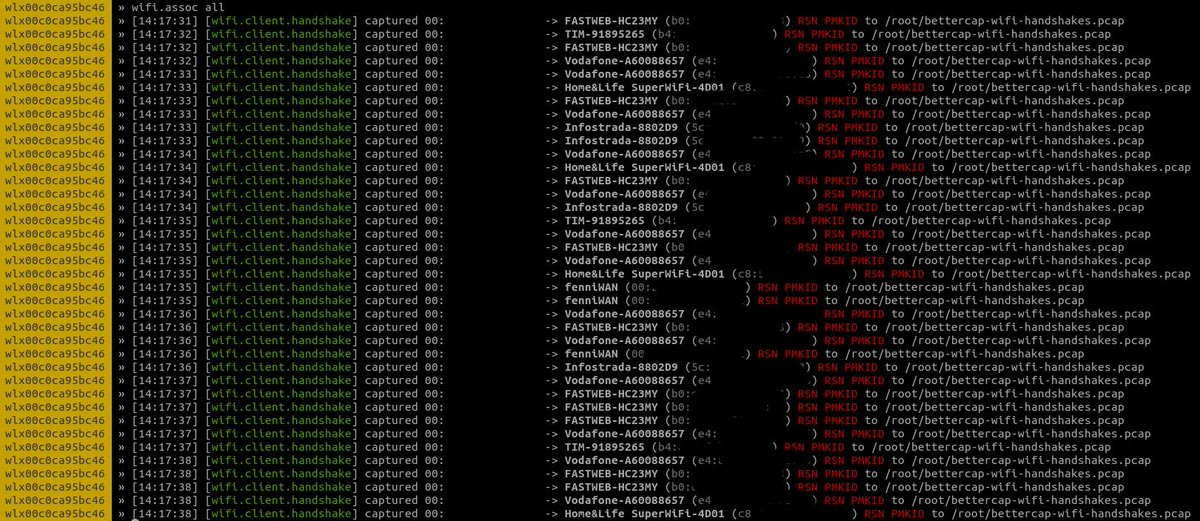
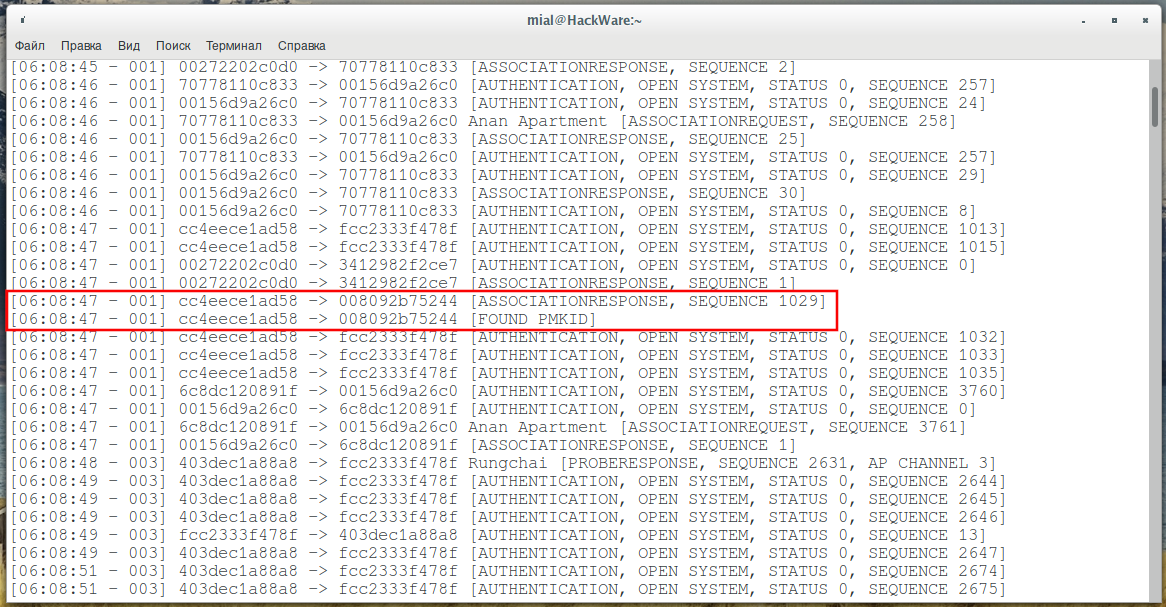
ALFA AWUS036NHA do not retrieve PMKID and keep factory MAC · Issue #182 · ZerBea/hcxdumptool · GitHub

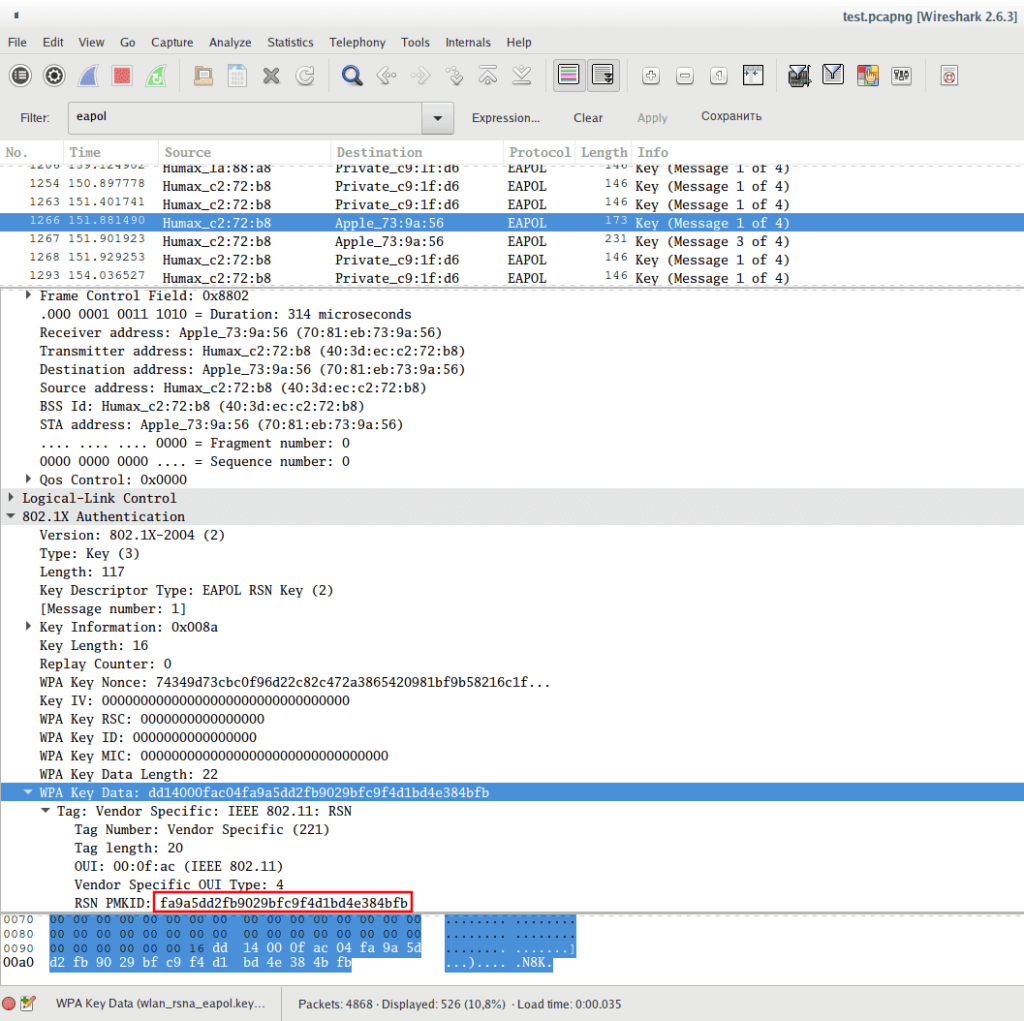
How to Hack Wi-Fi: Cracking WPA2 Passwords Using the New PMKID Hashcat Attack « Null Byte :: WonderHowTo

Encourage Hacking - How to Crack WPA2 Passwords Using the Latest PMKID Hashcat Attack A New Method of Password Cracking Rather than relying on intercepting two-way communications between Wi-Fi devices to try
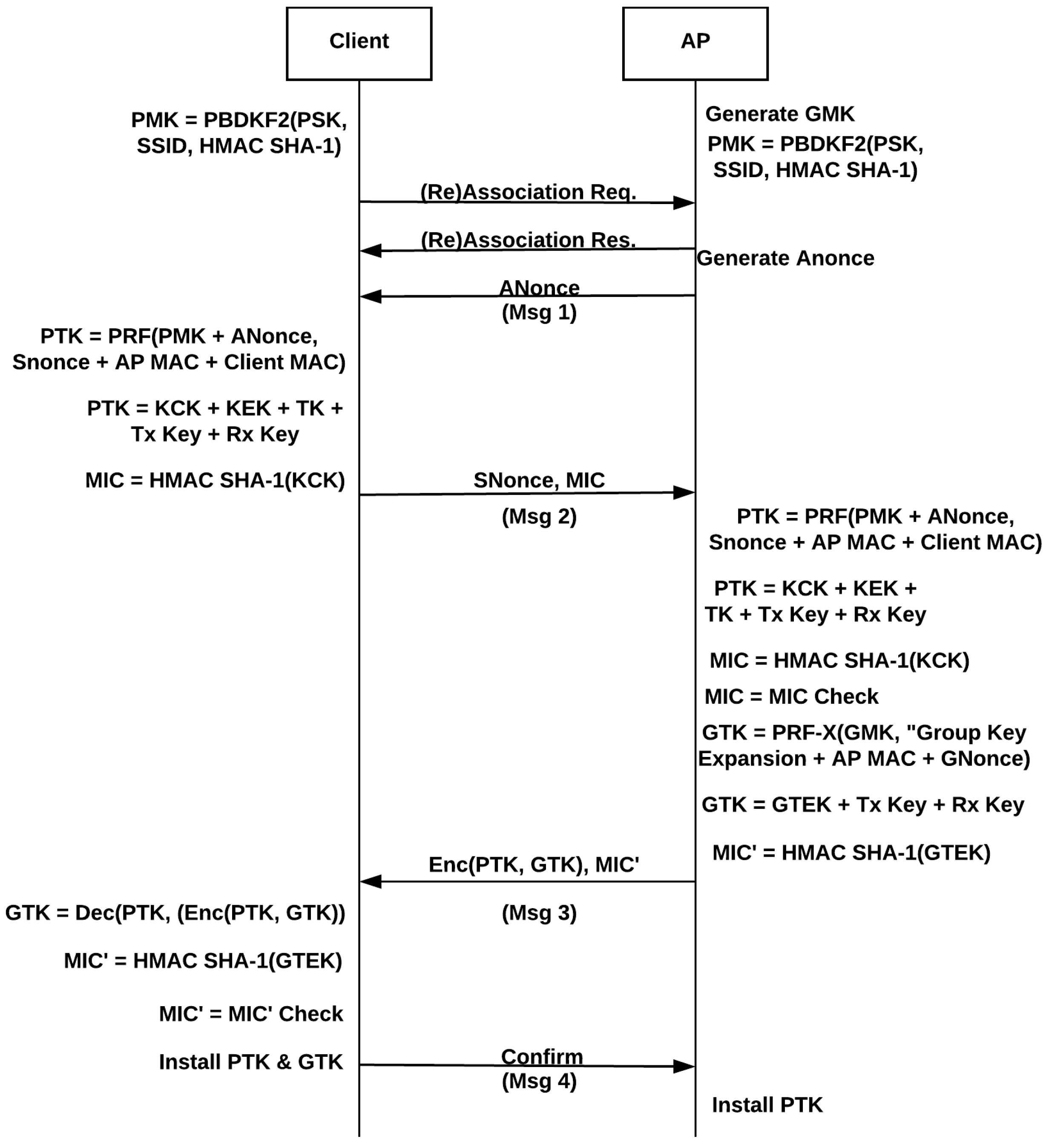
Electronics | Free Full-Text | A Comprehensive Attack Flow Model and Security Analysis for Wi-Fi and WPA3

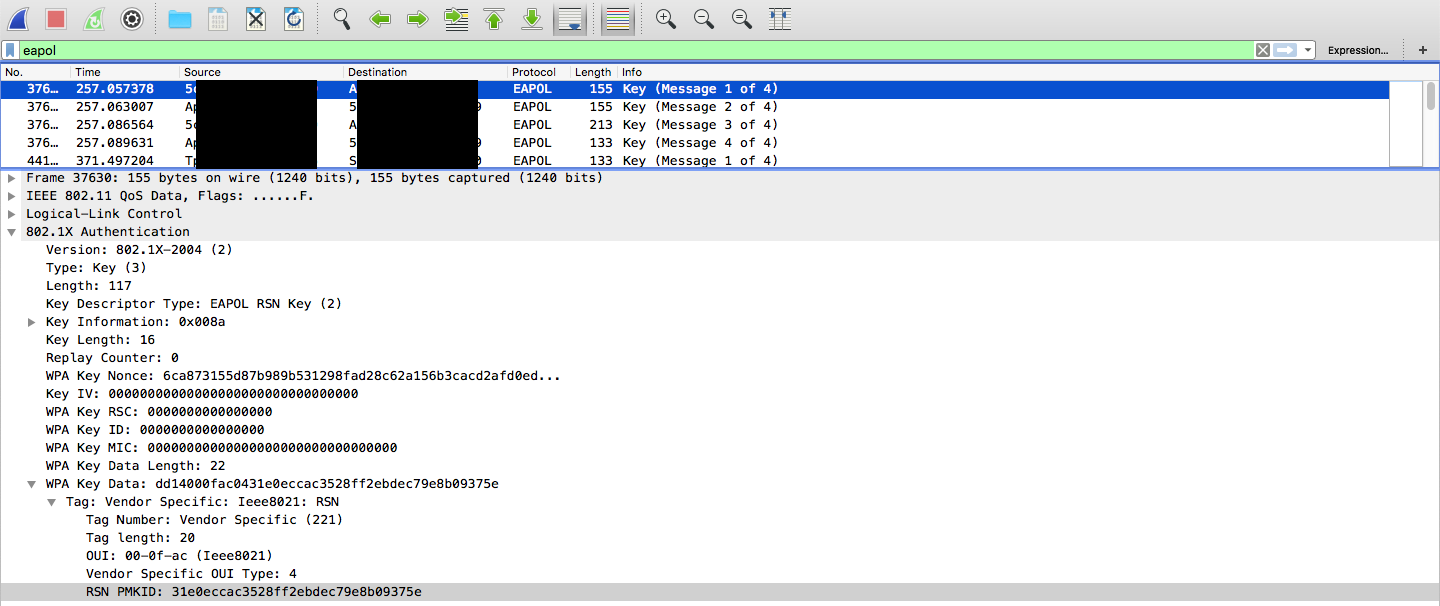






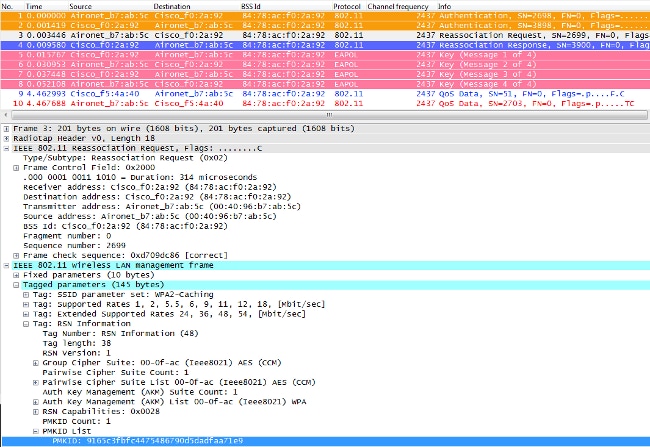
![Capturing WPA/WPA2 Handshake | Cracking Principles [CYBERPUNK ] Capturing WPA/WPA2 Handshake | Cracking Principles [CYBERPUNK ]](https://cdn.cyberpunk.rs/wp-content/uploads/2019/06/Capturing_WPA_WPA2_Handshake_bg.jpg)