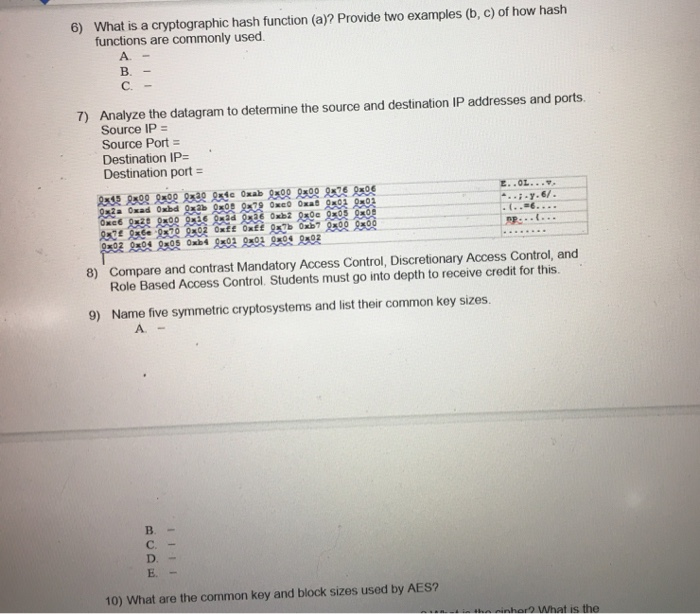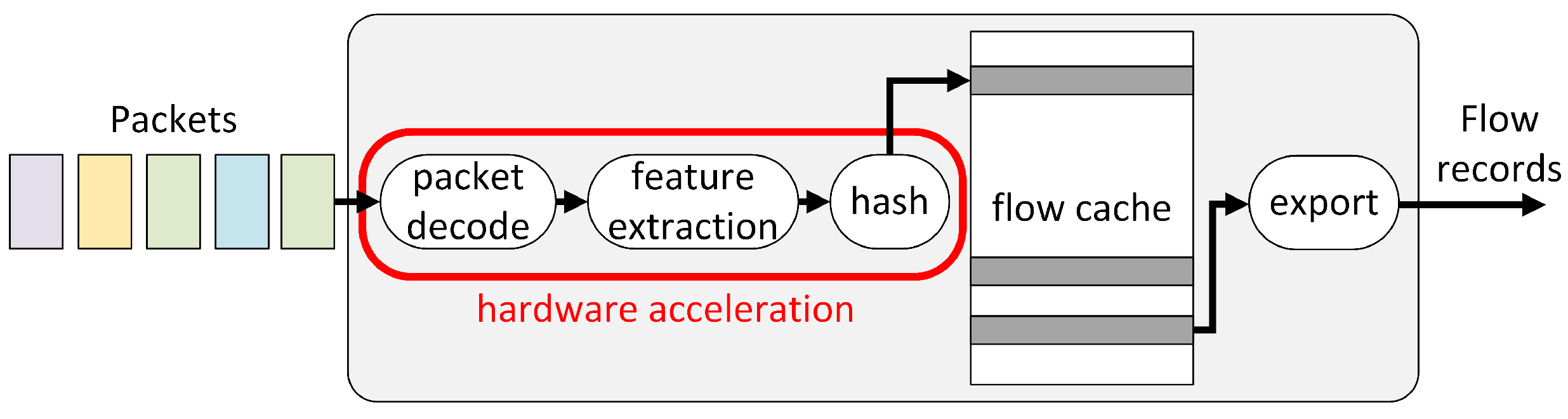
Electronics | Free Full-Text | Comparison of Hash Functions for Network Traffic Acquisition Using a Hardware-Accelerated Probe
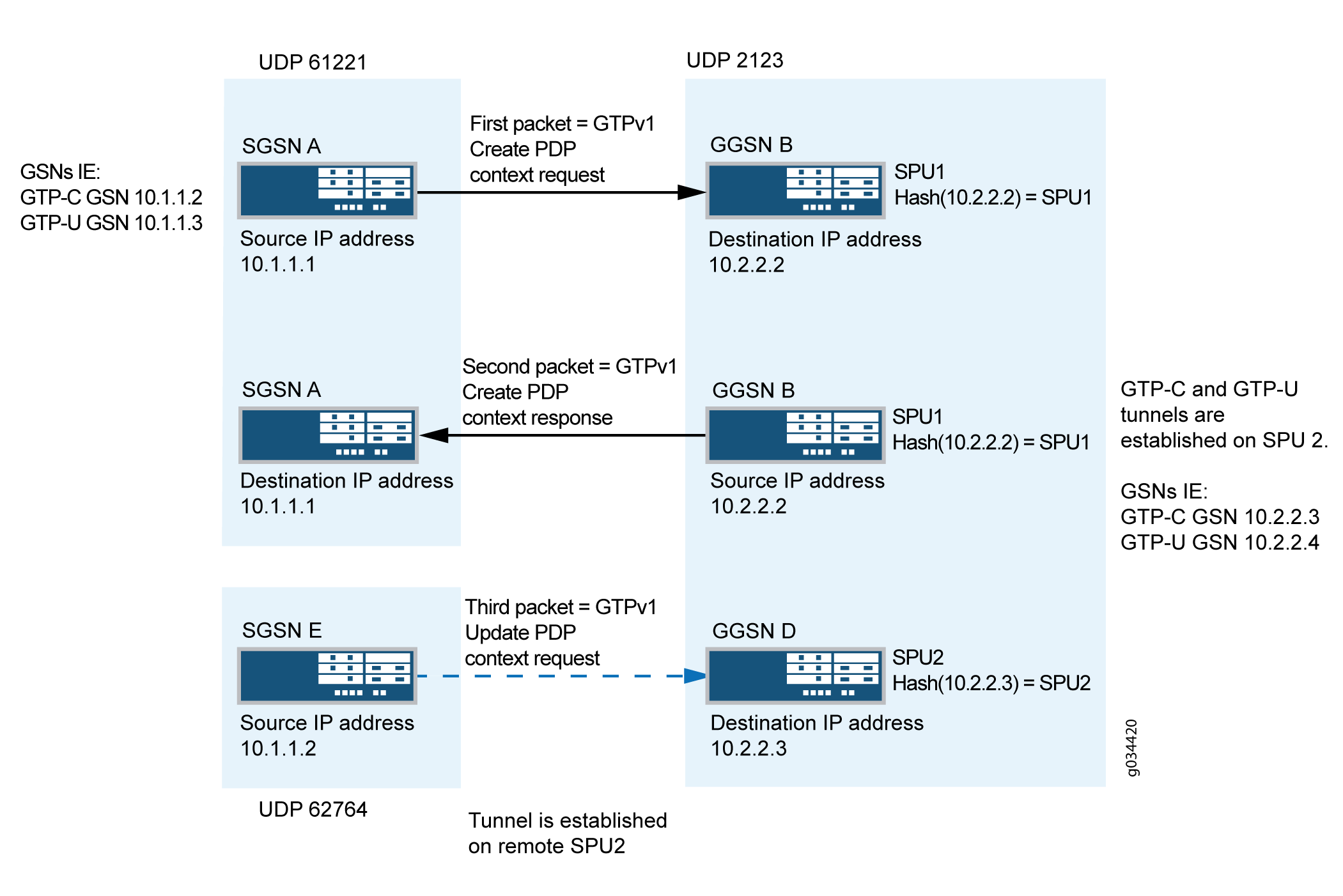
![Cisco Wireless Controller Configuration Guide, Release 8.5 - Mobility Groups [Cisco Wireless LAN Controller Software] - Cisco Cisco Wireless Controller Configuration Guide, Release 8.5 - Mobility Groups [Cisco Wireless LAN Controller Software] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/100001-200000/140001-150000/146001-147000/146597.jpg)
Cisco Wireless Controller Configuration Guide, Release 8.5 - Mobility Groups [Cisco Wireless LAN Controller Software] - Cisco

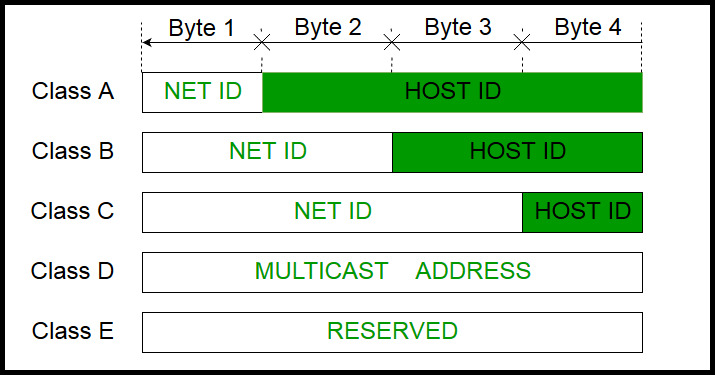
Diagram showing the hierarchy of network address entities for IP and... | Download Scientific Diagram

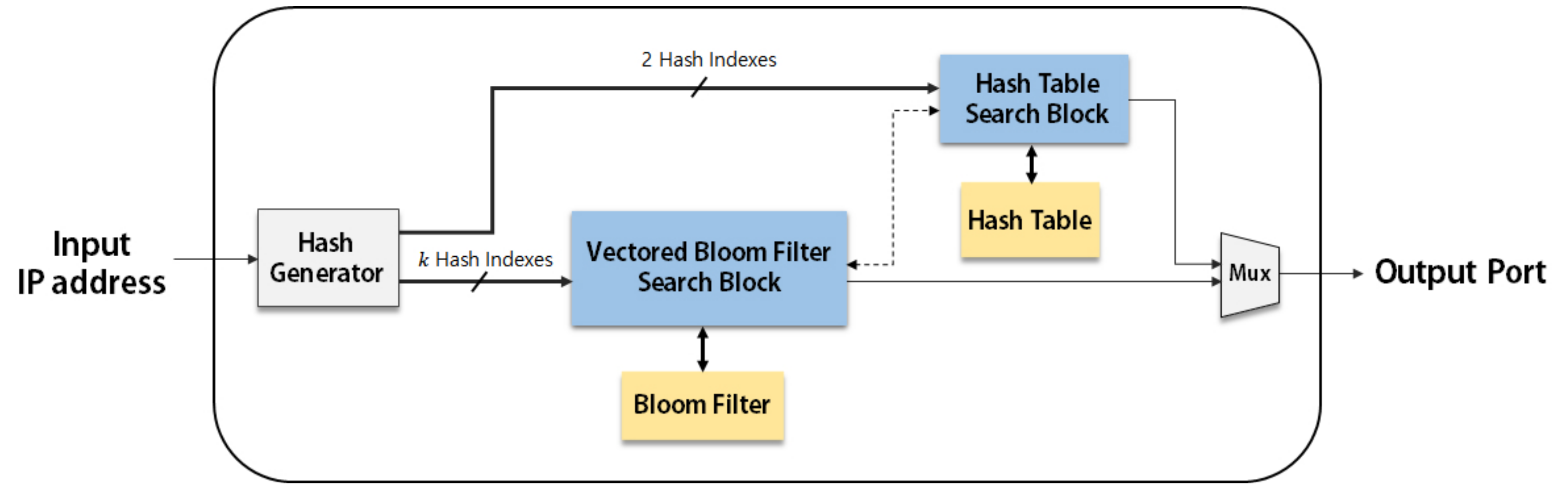
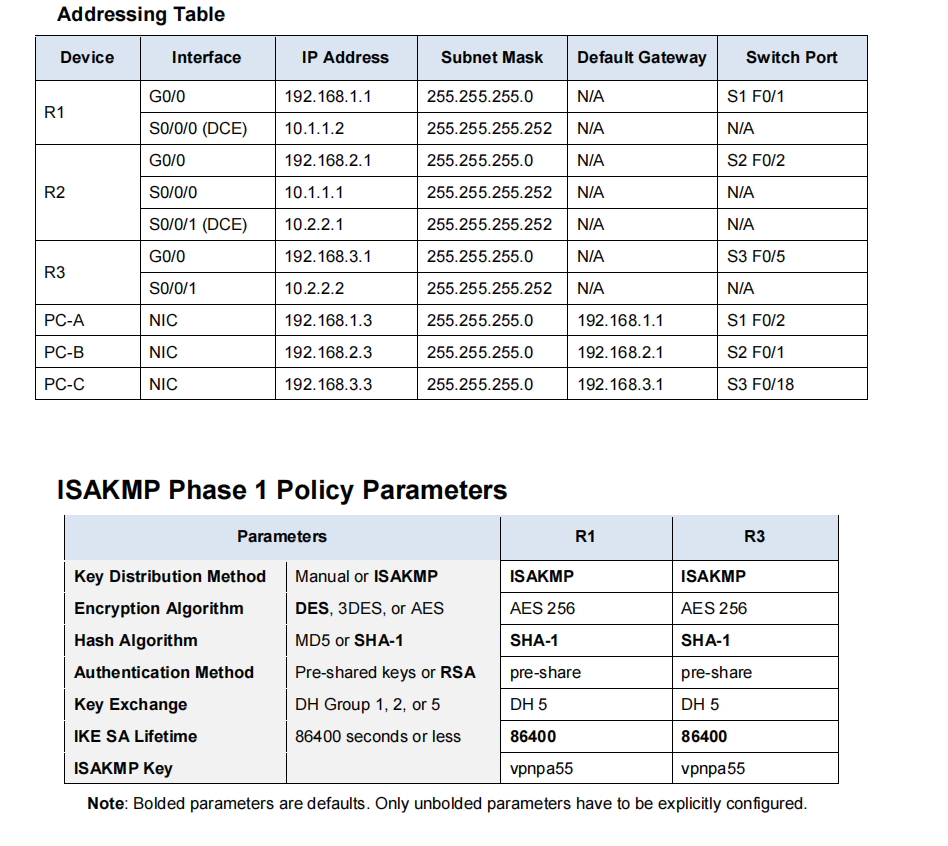
Applied Sciences | Free Full-Text | Vectored-Bloom Filter for IP Address Lookup: Algorithm and Hardware Architectures